In this article, I will be explaining what is a blockchain and how it works this will help you to set the foundation for understanding Blockchain Technology. Before going to explain, I’d like to mention a quote from the World Economic Forum.
Blockchain has the potential to transform how humans transact.
“It is a decentralized electronic ledger system that creates a cryptographically secure and immutable record of any transaction of value, whether it be money, goods, property, work or votes”
Reference: Building Blocks (chain)s for a Better Planet, World Economic Forum 2018.
This is a very loaded statement because it contains a lot of information, but as we move forward a lot of these elements are going to make sense to you and all of these elements & Terminologies are going to be cleared as simply as possible.
Now Let’s describe a blockchain, I want to share with you a simple example of a transaction of value between two parties in a Legacy or a classical business world.
Let’s assume that two parties want to do a transaction and transfer an asset of value; Party A wants to do a transaction to transfer an amount to Party B, so they need to both agree on the terms of the transaction and agree once the transaction is completed it’s treated final. Instead of recording the transaction on separate ledgers, Party A has a ledger of their own where they keep that transaction, they write down exactly how the transaction took place and Party B has also their ledger and they write in their ledger the transaction and what happened to it.
This is subject to errors because Party A may record the transfer a certain way, while Party B might have had a different process for recording transactions. So there may be some errors that lead to discrepancies between both parties. Party A may have a certain transaction record in their ledger, which is not exactly like the transaction recorded on Party B’s end, even though it’s the same transaction. It’s just that party A recorded it. One way Party B recorded differently. It could also be subject to tampering. Party B may turn around after the transaction took place and modify the details of the transaction in their ledger. Additionally, one of these ledgers could get lost, or there may be a system failure and it might be deleted. All of these transactions are risks associated with at present traditional transactional system.
What if instead of having these two separate ledgers, Both parties worked on a single ledger and that single ledger was shared, but not only shared between these two parties but there were multiple copies of that same ledger distributed across nodes/computers all over the world? Furthermore, the information that’s recorded on that ledger is recorded permanently, and the information is immutable. Immutable means that you can’t make any changes once it’s been recorded. In a nutshell, this is what a blockchain is.
Let me explain to you a definition of a blockchain. A blockchain is a constantly growing ledger that keeps a permanent record of all the transactions that have taken place in a secure, chronological, and immutable way. I’ll be describing what each of these elements means by putting some examples, in a nutshell, of a blockchain. All it is a ledger and It’s a file. The ledger that keeps track of all these transactions in this file and the blockchain is constantly growing.
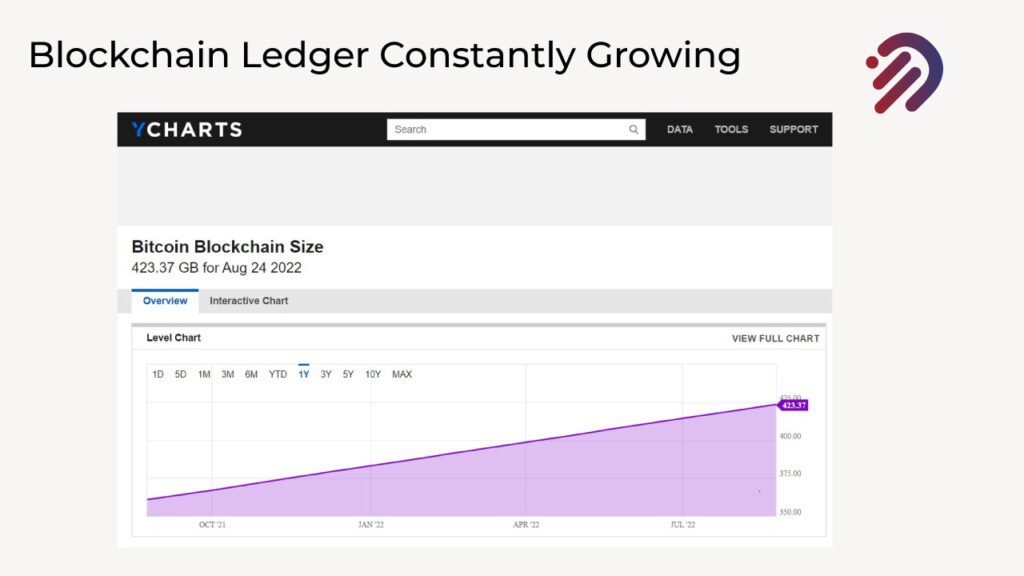
Let me show you some examples of real blockchain technology implemented in Bitcoin. Bitcoin is a cryptocurrency one of the key technologies that make bitcoin possible is blockchain technology. The Bitcoin Blockchain As of now is over 423 gigabytes in size. However not only, there are also thousands of copies of that same blockchain all around the world, and that blockchain keeps growing with every single transaction that gets done on the bitcoin network. New blocks get added and the blockchain keeps growing, that blockchain keeps a permanent record of all the transactions. Remember one thing we are just discussing blockchain technology not discussing the type of currency or mechanism of cryptocurrencies as they are popular right now and we will talk later on about their modality and currency acceptance based on currency rules and regulations according to the Islamic & Financial principles.
Blockchain is just a technology or architecture it can store different information, as you can use Blockchain in the supply chain You’ll be able to use a blockchain to record your supply chain transactions because the information recorded on a blockchain is secure.
It’s secure in many ways because you can keep multiple copies of that blockchain across multiple nodes all around the world. What you’re seeing here is a global map showing thousands of nodes in the bitcoin blockchain, which keeps a permanent record of the entire blockchain in bitcoin.
So what that means is that you don’t have a single point of failure because you have multiple copies of that blockchain. The information recorded on a blockchain is captured chronologically. What that means is that as transactions take place, they are recorded on the blockchain chronologically, which makes perfect sense and fits in a supply chain. Once that information is recorded, it is recorded immutably. That means you cannot make any changes to it.
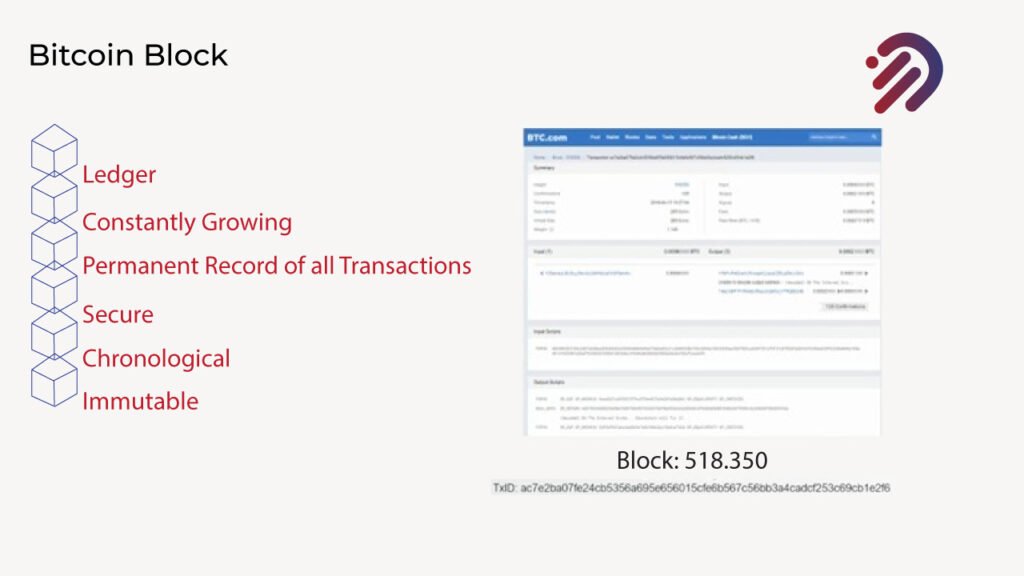
What you see right here is a transaction that took place on block number five hundred and eighteen thousand three hundred fifty-one the Bitcoin blockchain, where I stored a message. That message is recorded permanently and immutably on the bitcoin blockchain, and nobody will ever be able to change that because it is recorded permanently and immutably.
Now Let’s Explain basic blockchain cryptography concepts.
CRYPTOGRAPHY:
Cryptography refers to the study and application of techniques used to transmit, protect and store information and communications securely and privately to avoid being intercepted by third parties. That is an adversary. Now, some key terms that I want to tell you about.
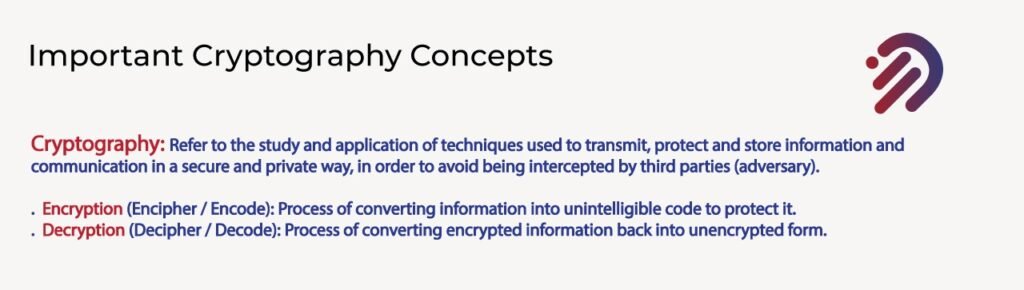
1. Encryption.
Encryption is also known as a cipher or in code, and it’s the process of converting information into unintelligible code to protect it. Now, if you encrypt something, you can decrypt it.
2. Decryption.
Decryption, also known as deciphering or decoding, is a process of converting encrypted information back into unencrypted form every time you are dealing with a website and you use your password.
What’s happening is that you are using cryptography. Let me explain how this applies in the context of blockchain. But by first giving you a basic example of encryption and decryption. So if I give you this specific example.
This is communication. But right now it is encrypted. You can’t understand what it says because I have encrypted it. I’ll now go through the process of decrypting it. So you see how it works to do this. I’m going to use what’s known as Caesar’s cipher. Now, a Caesar cipher is a type of substitution cipher in which each letter in plain text is replaced by a letter of some fixed number of positions down the alphabet. What do I mean by that? If you look at this Caesar cipher, what you find is that the letters on the outside that are uppercase are labeled as plaintext and the lowercase ones on the inside are cipher text. What that means is that the ciphertext will be the encrypted version, and the plain text version will be decrypted version just as some background Caesar ciphers have been around as far back as Julius Caesar, who used it in his private correspondence, and it was extremely well used for a very long time.

Let me use this specific example of how we’re going to use it for this example that I showed to you. If we turn the wheel and we turn it precisely 19 counterclockwise, you will replace the letter A. Which is the plain text with a lowercase t. The B would become u etc. This is what’s known as a key of 19. That is, we are moving. The Caesar Cipher 19 places counterclockwise so we can replace the letter a with lowercase t. And now we’ve got our decryption mechanism. So let’s apply that to the example we showed before. So if we follow that specific example, what we find is that it translates into this I have confidential information ‘XYZ’.

This example is what is known as shared secret cryptography, also known as symmetric cryptography. Because both the sender and the recipient of the message that is encryptor and the decryptor they use the same key. You need to know that the key is 19 to encrypt and decrypt it. This has vulnerabilities. I’ll give you one example.
Let’s assume that Yousuf wants to send the message to Ali, and he wants to encrypt it. Well, Ali doesn’t know the key yet. Somehow, Yousuf has to get that key over to Ali. Well, let’s bring in an adversary in this case Saniya. And let’s assume that while Yousuf is sending that key over to Ali, so he knows how to decrypt it.
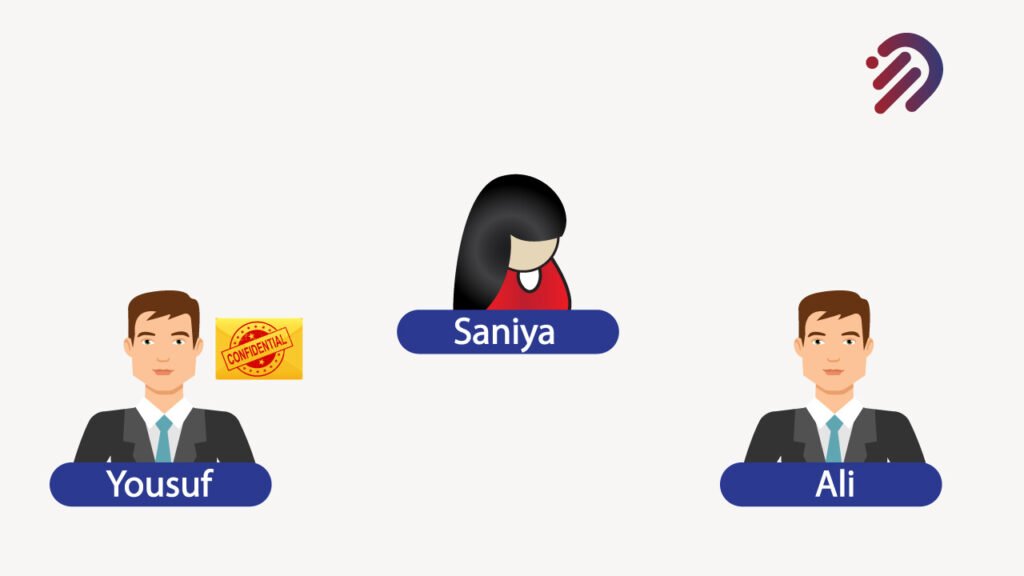
Saniya manages to get a hold of it. If that happens, then we have a big problem because Saniya can basically decrypt the messages and she could even replace them with her own. This is a huge vulnerability. And when you hear about sometimes websites getting hacked and millions of passwords lost often, is that shared secret passwords? And if somebody knows all the passwords and you can hack that source, you can steal all the passwords because of Shared secrets. That’s why shared secret cryptography does have some major vulnerabilities.

Now, let’s go into a different example. In this case, I want to go into what’s known as public key cryptography. And this is what’s used extensively in blockchain now. In that scenario, let’s assume that Yousuf wants to send the same message to Ali. We also have the same adversary, Saniya now for Yousuf to send that message to Ali. In that case, Ali has two keys a public key and a private key.
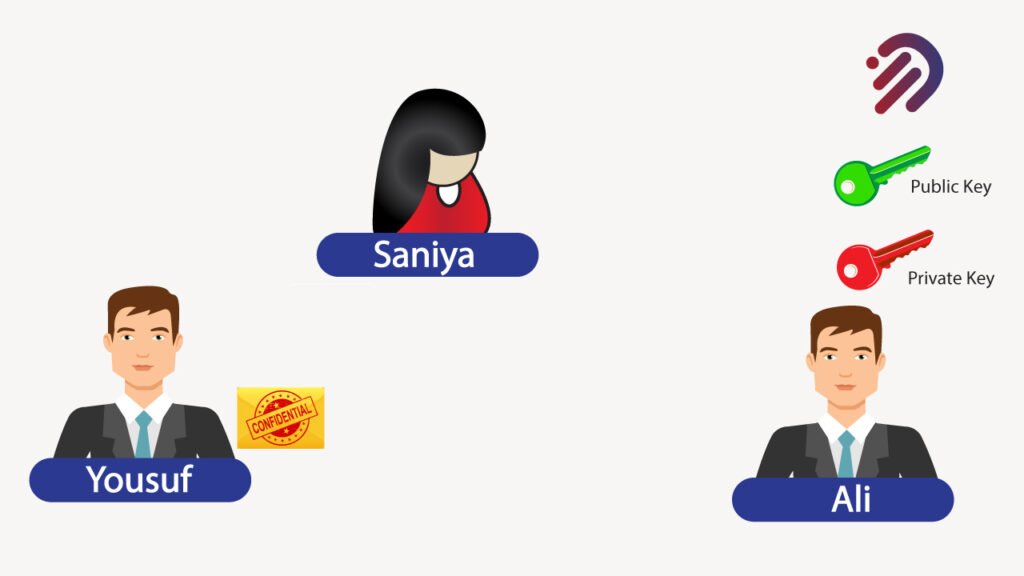
This is the public key cryptography component because the public key. Ali can share it with anybody. The purpose of the public key is merely to encrypt information right now. Yousuf can take that message and encrypt it using Ali’s public key. Now, Yousuf can then send the encrypted message over to Ali, and the only person that can read this is Ali because he has the private key for it.
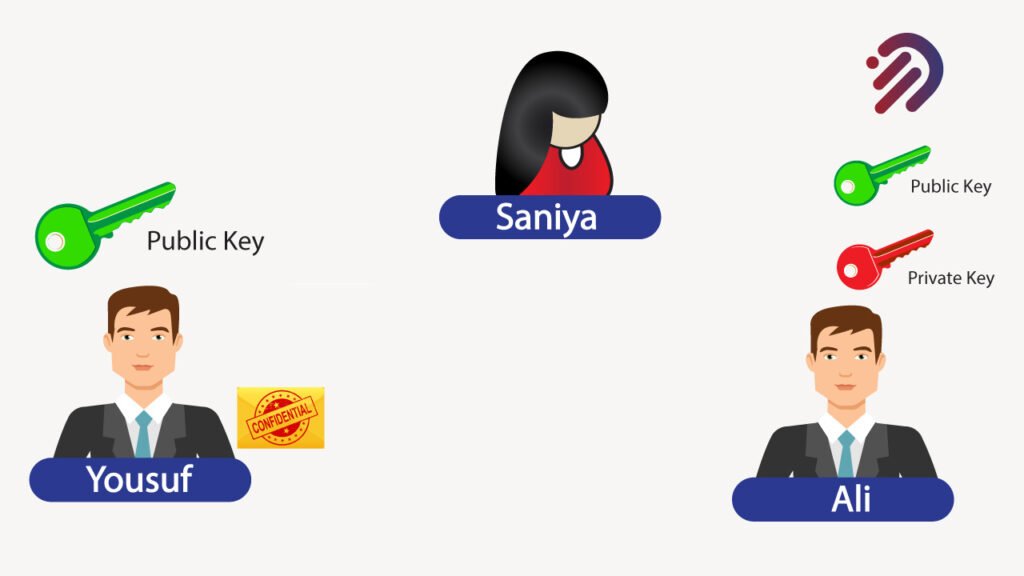
Furthermore, let’s assume that Saniya was able to get a hold of that public key. It doesn’t do anything for him. So the point is, that stealing a public key will not do her any good. That’s why it’s perfectly OK for Ali to share his public key with anybody because all it does is encrypt messages. Let me tell you a little bit more about public key cryptography.
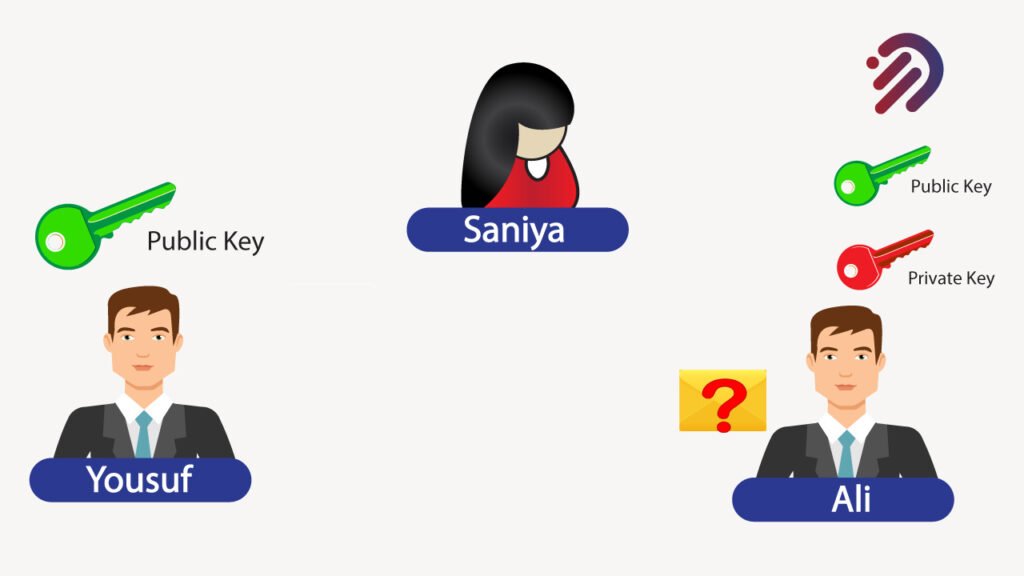
Public key cryptography, also known as asymmetric cryptography, is a cryptographic system that uses two keys a public key which allows anyone to encrypt the message and you can share it with anyone, and a private or secret key known only to the recipient of the message. Now, this public key cryptography uses two keys, as I mentioned a public key and a private key. The private key is kept secret by one individual. The public key can be shared with anybody. This is an alternative to shared secret or asymmetric cryptography. It’s extensively used in blockchain.
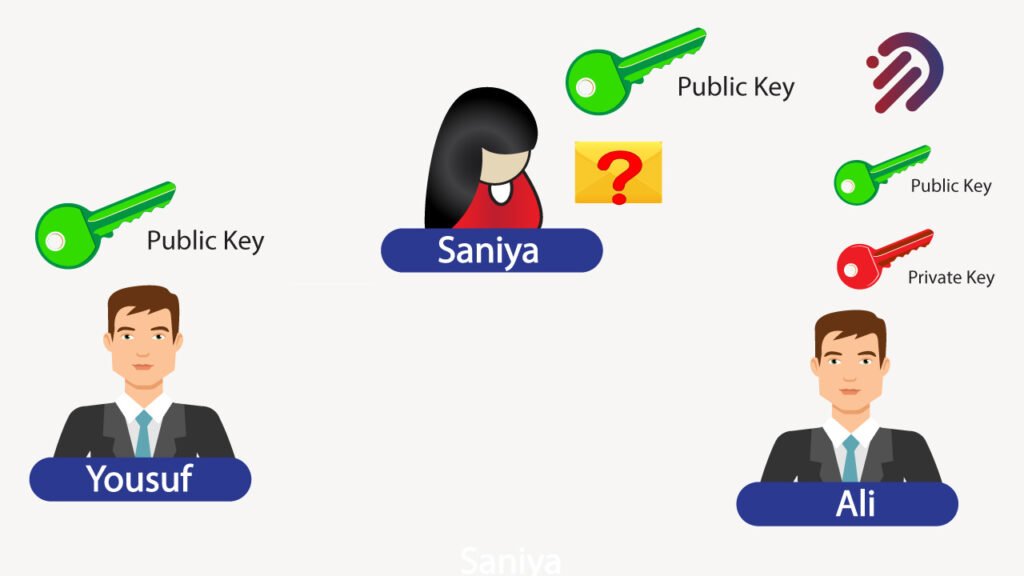
Furthermore, it’s used to generate digital signatures to validate the authenticity of data so that only the person that has the private key can sign a document. You can tell that that person is authentic because only that one person would be able to have the private key for that. Under that scenario, the public key would serve as a way of verifying that the person that signed that document is the authentic, genuine owner of that private key.

Now we’ve discussed encryption and encryption, we’ve discussed public key cryptography, and we’ve discussed digital signatures, which is the process to validate the integrity and authenticity of data.

Now I will tell you about another important concept, which is a cryptographic hash function. And this is critical in the concept of blockchain. A cryptographic hash function takes an input that is a message of any length and returns a fixed-size alphanumeric string called a hash value. This hash value serves as a digital fingerprint of the message. Let me give you an example of how that works.
For instance, if I write Hi with an uppercase h, it will give me this. That is a cryptographic hash.
Using what’s known as SHA256, SHA stands for the secure hash algorithm, and SHA256 is a type of cryptographic hash algorithm. There are others, but in this case, I’m showing you SHA256, which, by the way, is the same cryptographic hash that’s used in bitcoin.

Now, if I take hi and have two exclamation points after that, the cryptographic hash changes completely. Furthermore, I can put a much longer message, for instance, in this case, Ali had a little cat whose hair was white as snow. And you also can get a cryptographic hash for that in all cases. It’s a fixed-size alphanumeric string that doesn’t matter how long the string that you turn and you insert and convert into a cryptographic hash. You will always get a fixed-size alphanumeric string. As a quick demonstration of this concept of cryptographic hashes, I’m going to take you to a website for a blockchain demo and specifically a demo blockchain Hash, which has a SHA256 hash generator that you can use for free. What you will find is there’s a field that’s called data, and underneath that, you see a hash. What that means is that anything you place inside the data field, you will have a corresponding cryptographic hash on the bottom. In this case, an SHA256.
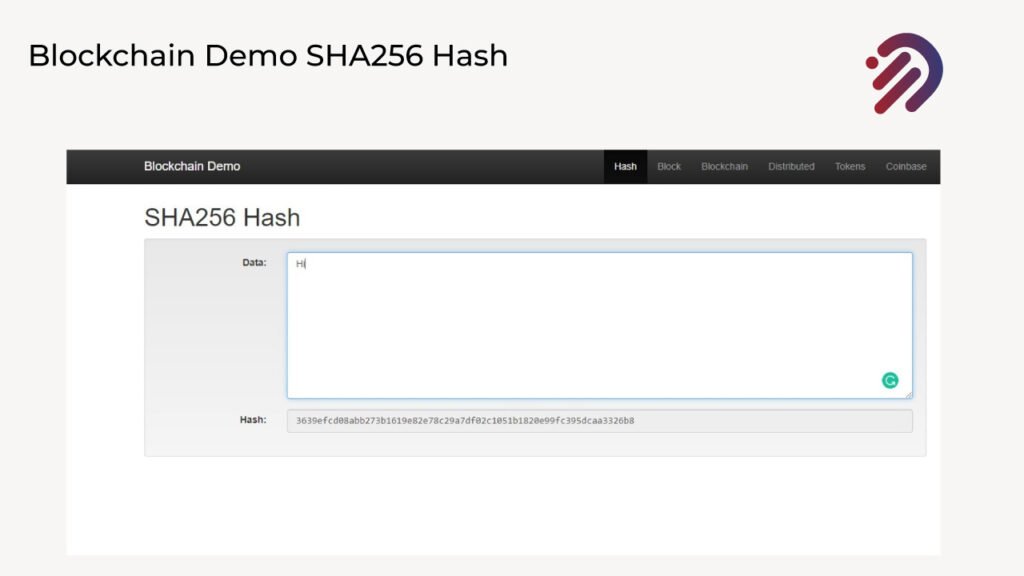
What you see here, starting with E3 b0, is the cryptographic hash for blank nothing. Now, if I were to add in here, as I mentioned the example hi with the uppercase H. You will find that you’re going to get exactly the cryptographic hash that I showed to you below.
But if I add two exclamation points, you see how it changes the values completely and you see you have a completely different cryptographic hash. And that’s because making any changes whatsoever in the data that you present to a cryptographic hash will make a dramatic change in the entire cryptographic hash that it gets. So the interesting thing is that you can place any amount of data here. For example, I’m going to paste the entire body of the Bitcoin white paper nine pages worth of it, and you will find that it has a corresponding cryptographic hash of a fixed size. What you find is that even the short little ones like hello and this long document give you the same fixed size, length, and alphanumeric string. Now, this is one of the advantages of using cryptographic hashes because you can take a massive amount of data and narrow it down to a fixed-size alphanumeric string. So putting it into context, cryptographic hash functions generate a digital fingerprint or a message digest. And the way they do that is that they will always generate the same result which is called deterministic. But it means that no matter what amount of data you place to generate a cryptographic hash, you will always get that corresponding cryptographic hash for that data. And if any change were made, no matter how small, you would come up with a completely different hash value.
The advantage of these cryptographic hash functions is that they’re easy to calculate for any amount of data. Furthermore, they will not generate the same hash for two different inputs.

This is known as collision resistance. Cryptographic hash functions are what are known as one-way functions. This is different from encryption and decryption. You see, when you take a message and you encrypt it, you can decrypt that message. That is, that can encrypt the message, and you can find a way to decrypt it back to the original message. This is different from cryptographic hash functions, because when you create a SHA256, for instance, a hash of a certain amount of data, there’s no way for you to extract that certain amount of data from that cryptographic hash.
In other words, it’s a one-way function. This is critical in authenticating and verifying the integrity of a set of data because a cryptographic hash function can serve as a digital fingerprint of that specific data. Let’s see how these cryptographic hash functions tie into blocks in the blockchain.
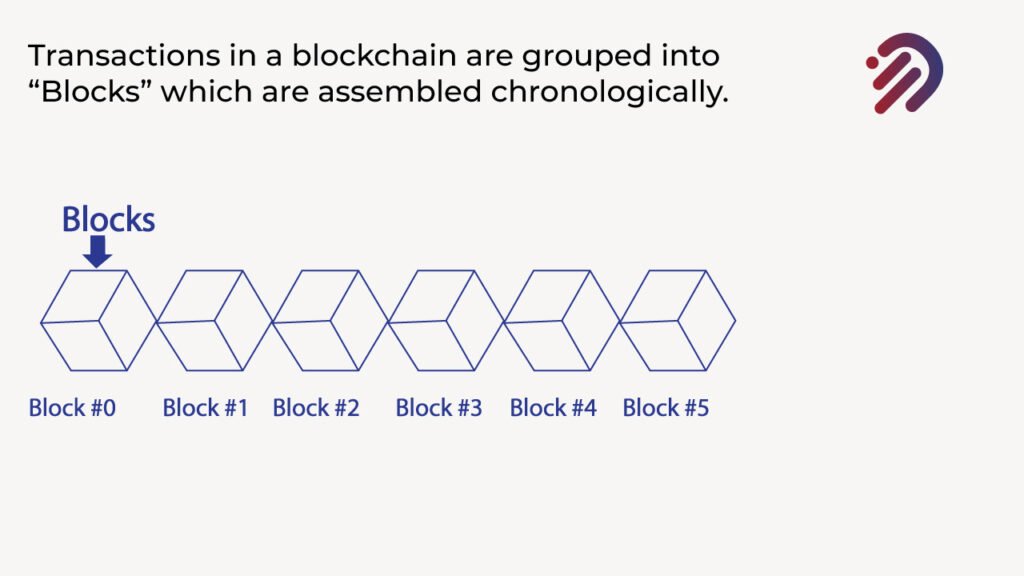
The transactions are grouped into blocks, and these blocks are assembled chronologically. A block of transactions follows another block of transactions, and they’re ordered chronologically. These blocks are all linked together using cryptographic hashes. That is, the block from Block Zero has a cryptographic hash, and that cryptographic hash is part of the data of block number one.
Then that block no one will have a new cryptographic hash corresponding the block number one. You will do the same thing with block number two, then block number three block number for block number four. So what you’re doing is building a chain of blocks that are all linked together using cryptographic hashes.
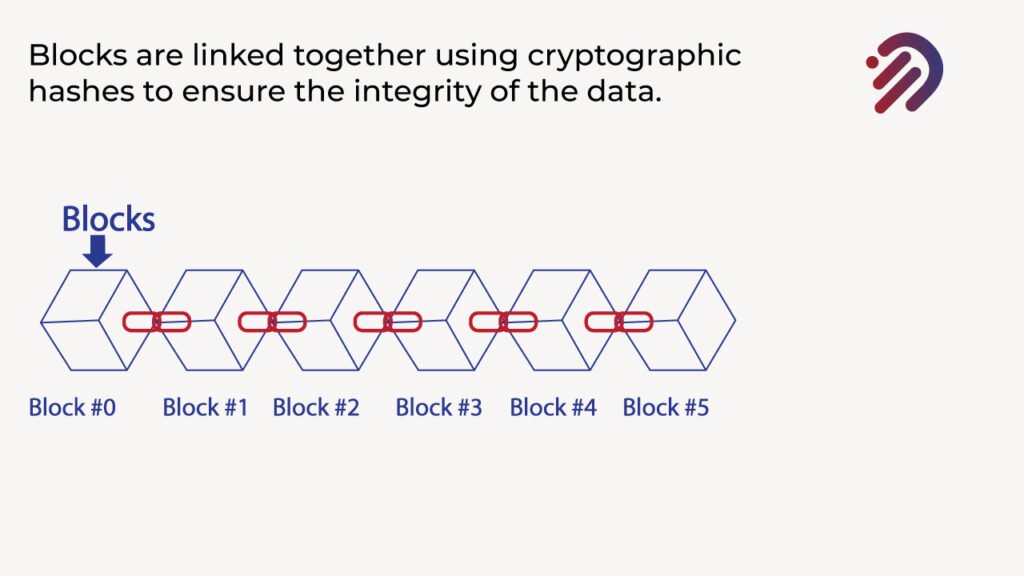
Now what this means is that if anybody tries to modify any info in the blockchain, it will change the cryptographic hashes in the chain, making it obvious that hasn’t been tampered with. So, for instance, if anybody wanted to change anything, say, for example, in block number two, that would change the cryptographic hash for block number two, which as a result would change the cryptographic hash or block number three. As a result, would change a cryptographic hash block number four, then block number five, etc. And this is why cryptographic hashes are so important in preserving the integrity of the information that’s recorded on the blockchain.

THE ROLE OF LEDGERS IN BLOCKCHAIN.
Earlier we discussed about blockchain has shared ledgers. Let’s explain the role of ledgers in businesses. Ledgers are used in businesses to record business activities. That is when a business does any type of transaction or performs any type of activity. That information is recorded on ledgers. Each business defines its ledgers. If you’re actually into the Oil Industry, your ledger captures a certain amount of information that will be completely different from a company that’s in the pharmaceutical industry. It’s just each ledger is defined by the business types that are running it. Furthermore, ledgers track the transfers of assets. If you’re in the oil industry, for example, your ledger would be capturing how many barrels of oil are transferred to another party. If you’re in the pharmaceutical industry, how much of a certain prescription is being transferred to the distributors? All of these transfers are recorded on ledgers. Ledgers are everywhere.
For instance, Ali may have a record at his bank of how much money he has but for example, David may have a different bank, and that bank keeps a record of how much money David has. And Ali is a different perspective. This leads to discrepancies in these ledgers. For instance, if Ali is doing a transfer to David some money, well, Ali’s bank will need to notify David’s Bank that he’s doing a transfer. So it might take several days while a check clears, while both banks agree on whether the check had any funds. And then the other bank reports that the funds were received, so this yields two discrepancies in ledgers. These result in errors. They yield inefficiencies and could be subject to manipulation. Sometimes somebody may try to run two checks or try to do multiple things, try to game the system because you have multiple different ledgers. Many discrepancies could show up, and these are vulnerabilities now in the blockchain. There is the only solution for mitigating the risk of discrepancies and security is Blockchain because it has distributed ledger.
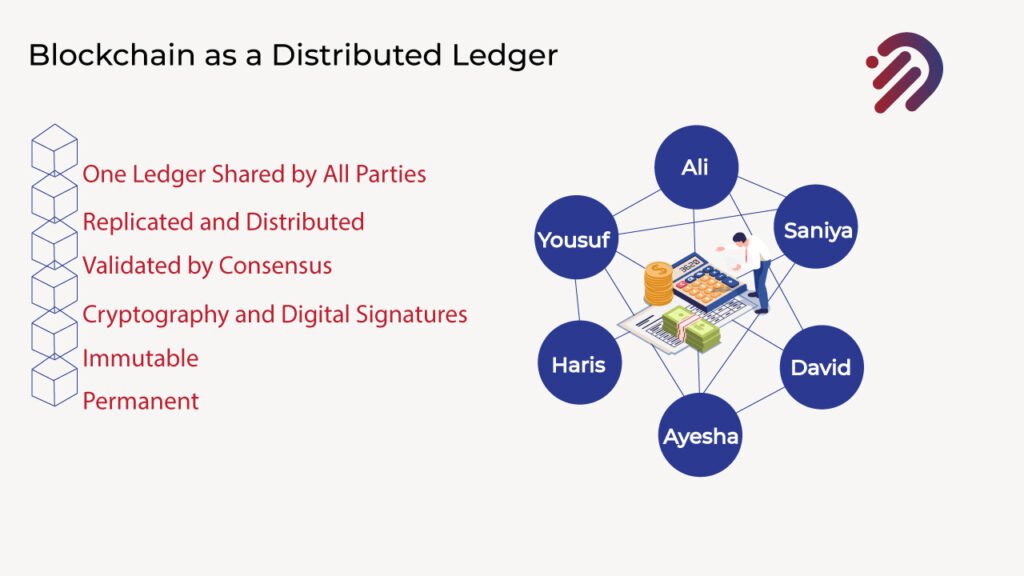
There’s a single ledger that everybody has. There’s one ledger that’s shared by all the parties. But that one ledger is replicated and distributed across many different computer systems or nodes. So there’s not just one copy of that blockchain. There are multiple copies of that blockchain, and all of the copies of that blockchain are kept in sync and validated through the process, known as consensus. Consensus is when all parties agree on what the contents of that distributed ledger are. There is one single source of truth that everybody agrees upon, and that source of truth that’s captured within the blockchain is protected through the use of cryptography and digital signatures. Furthermore, the information recorded on a blockchain is recorded in an immutable manner that is once it’s recorded. You cannot change it. and finally, that information is recorded permanently so this is immutable.
TOKENIZATION
Let’s discuss one of the key components that enable blockchain, especially in the Supply Chain is Tokenization. It’s tracking real assets in the world real assets are digital assets like ownership of any digital assets or currency like Bitcoin. So let’s explain first with the very very basic use of a token. in this case, we’re going to discuss a bitcoin. A bitcoin is a digital asset of value when you send that bitcoin to someone else, what you’re doing is transferring that digital asset of value to someone else.
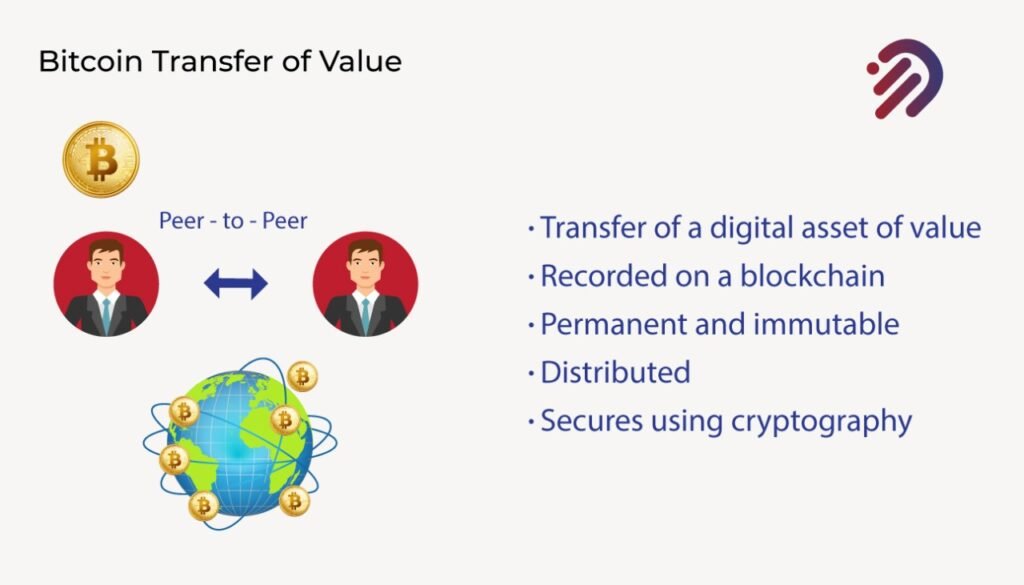
For instance, if I have a bitcoin and I send that bitcoin to someone else, I am transferring directly peer to peer that bitcoin to someone else. I am giving ownership of that bitcoin to someone else. This is very important because what bitcoin enabled for the first time through the use of blockchain is to be the ability to create a unique asset of value and be able to assign ownership to it and transfer it to someone else. The key problem with digital assets is that if you take any data, you can make multiple copies of it.
Let’s take another example, if I take a photo of something, I can take that photo and I can email it to someone else. Well, there’s a problem. I’m not sending the photo to someone else. I’m sending a copy of that photo. The original data for that photo is still on my computer, which is one of the problems how you saw that the film industry went through the entire disruption because when people were able to convert a video into an MP4 and make multiple copies of that MP4, you could just give that video away to everybody else. That’s impossible if you’re dealing with money.
So why bitcoin is so valuable is that if I have a bitcoin and I send that bitcoin to someone else, it’s very important. I no longer have that bitcoin. And one of the key ways that are accomplished is through the use of blockchain and recording that transfer on a blockchain, the recording of that information on a blockchain is permanent and immutable, and that blockchain is copied and distributed across multiple computers or nodes all around the world. And the information is secured using cryptography and ownership transfer digitally through tokenization. Tokenization is a process that converts the rights and benefits of a particular unit of value, such as an asset into a digital token that lives on the Bitcoin blockchain. Tokenization further enables the splitting of substantial, non-liquid assets into smaller and more liquid segments. Tokenization can also apply to physical assets as we will be discussing in detail in our next article “How Blockchain Applies in Supply Chain“. if you have any questions feel free to comment or contact me through email at yousuf@infotechabout.com






